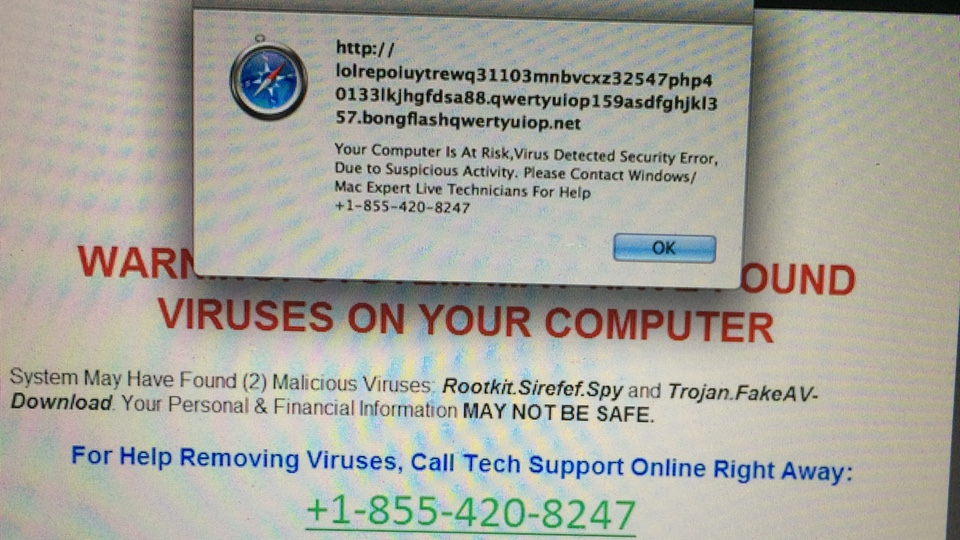
A reader passed along an information on a scam site targeting Mac users.
The site address is applesecurityissue.com
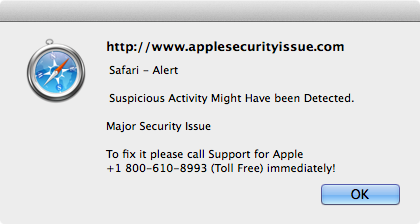
Quick search on the phone number 1-800-610-8993 yields one discussion at Apple Support Communities, so far. The site itself was registered on September 4, 2014 and updated today, September 18, 2014.
Whois information on applesecurityissue.com:
Whois Server Version 2.0
Domain names in the .com and .net domains can now be registered
with many different competing registrars. Go to http://www.internic.net
for detailed information.
Domain Name: APPLESECURITYISSUE.COM
Registrar: GODADDY.COM, LLC
Whois Server: whois.godaddy.com
Referral URL: http://registrar.godaddy.com
Name Server: NS17.JIXHOST.COM
Name Server: NS18.JIXHOST.COM
Status: clientDeleteProhibited
Status: clientRenewProhibited
Status: clientTransferProhibited
Status: clientUpdateProhibited
Updated Date: 18-sep-2014
Creation Date: 04-sep-2014
Expiration Date: 04-sep-2015
>>> Last update of whois database: Thu, 18 Sep 2014 20:01:06 UTC <<<
NOTICE: The expiration date displayed in this record is the date the
registrar’s sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant’s agreement with the sponsoring
registrar. Users may consult the sponsoring registrar’s Whois database to
view the registrar’s reported date of expiration for this registration.
TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services’ (“VeriSign”) Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.
The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
Domain Name: APPLESECURITYISSUE.COM
Registry Domain ID: 1874184235_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: http://www.godaddy.com
Update Date: 2014-09-04 11:22:40
Creation Date: 2014-09-04 11:22:40
Registrar Registration Expiration Date: 2015-09-04 11:22:40
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: abuse@godaddy.com
Registrar Abuse Contact Phone: +1.480-624-2505
Domain Status: clientTransferProhibited
Domain Status: clientUpdateProhibited
Domain Status: clientRenewProhibited
Domain Status: clientDeleteProhibited
Registry Registrant ID:
Registrant Name: Gaurav Kumar
Registrant Organization:
Registrant Street: New Delhi
Registrant City: Delhi
Registrant State/Province: Delhi
Registrant Postal Code: 110018
Registrant Country: India
Registrant Phone: +91.1234567890
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: gautam@webcreationindia.co.in
Registry Admin ID:
Admin Name: Gaurav Kumar
Admin Organization:
Admin Street: New Delhi
Admin City: Delhi
Admin State/Province: Delhi
Admin Postal Code: 110018
Admin Country: India
Admin Phone: +91.1234567890
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: gautam@webcreationindia.co.in
Registry Tech ID:
Tech Name: Gaurav Kumar
Tech Organization:
Tech Street: New Delhi
Tech City: Delhi
Tech State/Province: Delhi
Tech Postal Code: 110018
Tech Country: India
Tech Phone: +91.1234567890
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: gautam@webcreationindia.co.in
Name Server: NS17.JIXHOST.COM
Name Server: NS18.JIXHOST.COM
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
Last update of WHOIS database: 2014-09-18T20:00:00Z
The data contained in GoDaddy.com, LLC’s WhoIs database,
while believed by the company to be reliable, is provided “as is”
with no guarantee or warranties regarding its accuracy. This
information is provided for the sole purpose of assisting you
in obtaining information about domain name registration records.
Any use of this data for any other purpose is expressly forbidden without the prior written
permission of GoDaddy.com, LLC. By submitting an inquiry,
you agree to these terms of usage and limitations of warranty. In particular,
you agree not to use this data to allow, enable, or otherwise make possible,
dissemination or collection of this data, in part or in its entirety, for any
purpose, such as the transmission of unsolicited advertising and
and solicitations of any kind, including spam. You further agree
not to use this data to enable high volume, automated or robotic electronic
processes designed to collect or compile this data for any purpose,
including mining this data for your own personal or commercial purposes.
Please note: the registrant of the domain name is specified
in the “registrant” section. In most cases, GoDaddy.com, LLC
is not the registrant of domain names listed in this database.