Oracle releases Java 7 Update 11 to address vulnerability. If you do not need Java at all, it is advisable to uninstall it completely.
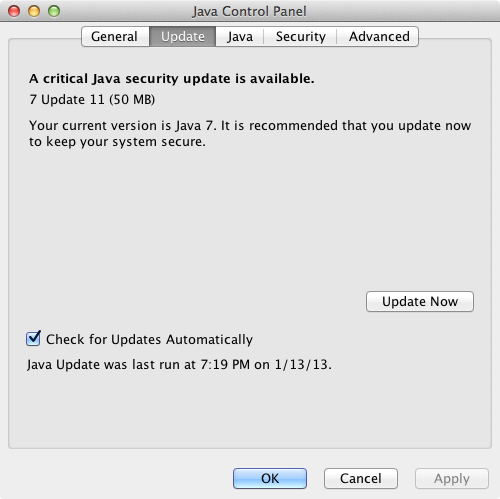
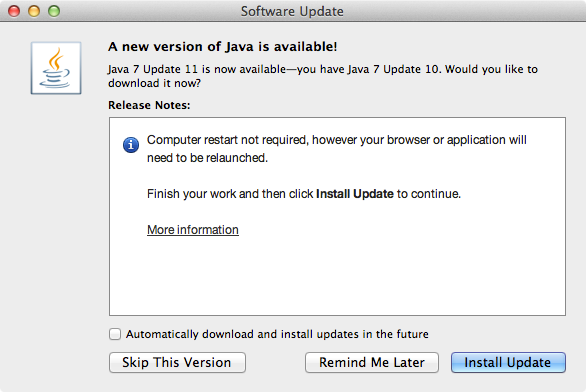
If the auto update failed, download Java 7 Update 11 manually.

Celebrating 20 years of Nonsense, Powered by Natural Intelligence.
Oracle releases Java 7 Update 11 to address vulnerability. If you do not need Java at all, it is advisable to uninstall it completely.


If the auto update failed, download Java 7 Update 11 manually.

Current news about Java vulnerabilities have been the talk of both tech and mainstream press. The U.S. Department of Homeland Security issued a warning of this vulnerability on Thursday January 10, 2013. On Friday January 11, 2013 we received numbers of called from users that their computers were infected by malware on that day. Security softwares such as Malwarebytes Anti-Malware and Microsoft Security Essentials detected the presence of malicious Java codes in the computers.
Companies like Apple and Mozilla Foundation have been pro-actively blocked Java on their platform.
This is certainly not the first time Java has been exploited to deliver malware. Back in August 2012 similar outbreak of malware used Java vulnerability as point of entry. Oracle says that they are preparing an update to Java to address the vulnerability.
So, I have successfully removed the ransomware/malware form the infected computer.
Booting the computer up to Safe Mode or Safe Mode with Networking would still activate the malware. That’s because it replaces the registry entry for Windows Shell from “Explorer.exe” to something else. So, boot the computer to “Safe Mode with Command Prompt” and type “regedit.exe” at the command prompt.
In registry editor, go to:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogon
In this particular case it was replaced with:
C:PROGRA~3dsgsdgdsgdsgw.bat
Delete the entry and replace it with:
Explorer.exe
Reboot the computer into “Safe Mode with Networking” and launch a web browser. Download, install and run the following programs if you haven’t already:
There are also other programs to scan and remove the malware.
Combofix detects that userinit.exe s also infected.
Microsoft Security Essentials also detected presence of Trojan:JS/Reveton.A, which was detected on January 11, 2013.
This computer was infected on Friday January 11, 2013, shortly after news about Java vulnerability was reported. After further investigations, I found that the infection happened through Java vulnerability. The infected computer had both Java 6 and 7 installed. Malwarebytes AntiMalware Free detected and removed the malicious Java module. Similar vulnerability was found back in August 2012.
Let’s take a look at the ransomware/malware.
It takes over Windows User Interface (UI) and replaces windows shell with the threatening message purporting from United States Department of Justice: “YOUR COMPUTER HAS BEEN LOCKED”
The message says that the computer has been locked for one or more violations:
They are pretty much the same language used in other ransomware/malware purporting from FBI, Police Cybercrime Investigation Department, etc. Some people might fall for this.
The malware also tries to activate the computer camera, for the purpose of scaring the user. Even though the infected computer doesn’t have any cameras installed, the malware pretends that it is recording video of the user.
The malware demands $300 to be paid in MoneyPak so users can unlock the computer.
So convenient that the malware tells you where to get this MoneyPak.
Anyway, you need to disable Java from your browsers.
If you’re using Mozilla Firefox, follow the instruction here: How to turn off Java applets
If you’re using Google Chrome, go to:
Settings > Privacy > Content Settings > Plug-ins > select “Click to play”
Also go to chrome://plugins/ to manually disable Java if necessary. (type in chrome://plugins/ in the address bar / omnibox)
If you are using Safari, go to:
Preferences > Security > uncheck “Enable Java”
If you are using Internet Explorer, follow the instruction from Sophos.
I’ve gotten a call earlier today from a friend because his computer has been locked by “The United States Department of Justice”. In addition to that “The United States Department of Justice” demands computer owner to pay $300 to unlock the computer “avoid other legal consequences”.
First and foremost, The United States Department of Justice does not run such operation.
This is a ransomware. It replaces Windows 7 shell with its own executable file. Booting the computer to plain “Safe Mode” or” Safe Mode with Networking” will load the malicious executable. Instead, boot to “Safe Mode with Command Prompt” and manually remove the malicious software.
I’ll describe what I did in the next post.
From GigaOM:
Nokia has confirmed reports that its Xpress Browser decrypts data that flows through HTTPS connections – that includes the connections set up for banking sessions, encrypted email and more. However, it insists that there’s no need for users to panic because it would never access customers’ encrypted data.
Nokia is playing the role of the man in the middle with the Xpress Browser. Nokia installs its own SSL/TLS certificate in the XPress Browser so it could create a secure/encrypted session to Nokia’s own server. The server then initiates https session with the website.
Does anyone remember what Opera Mini does?
Some corporate networks use proxy that request https session on the proxy on behalf of the computers in their networks.
We had a request from someone to stop AirPort Express broadcasting the SSID, for security purpose.
Hiding Wireless network SSID does not really enhance security.
Unfortunately, this tactic may lead to a false sense of security, as it only impedes casual wireless snooping, and does not stop a determined attack on the network.
There are numerous of tools that can scan any hidden SSID.
Just in case anyone still want to hide their AirPort Express or AirPort Extreme SSID:
In AirPort Utility, go to “Wireless” and click on “Wireless Options…”
Check the box for “Create hidden network”
Someone sent me a direct Twitter message with a link to a Facebook App. I don’t have Facebook account. Apparently Facebook do not want a cat to open an account. Anyway, as a Tech-savvy cat I investigated the link and it tried to redirect to some site.
meow-os-x:~ meatloaftcat$ whois factoryonlinegall.com
Whois Server Version 2.0
Domain names in the .com and .net domains can now be registered
with many different competing registrars. Go to http://www.internic.net
for detailed information.Domain Name: FACTORYONLINEGALL.COM
Registrar: ENOM, INC.
Whois Server: whois.enom.com
Referral URL: http://www.enom.com
Name Server: NS1.2X4HOSTING.RU
Name Server: NS2.2X4HOSTING.RU
Status: clientTransferProhibited
Updated Date: 26-dec-2012
Creation Date: 26-dec-2012
Expiration Date: 26-dec-2013>>> Last update of whois database: Fri, 28 Dec 2012 23:01:18 UTC <<<
NOTICE: The expiration date displayed in this record is the date the
registrar’s sponsorship of the domain name registration in the registry is
currently set to expire. This date does not necessarily reflect the expiration
date of the domain name registrant’s agreement with the sponsoring
registrar. Users may consult the sponsoring registrar’s Whois database to
view the registrar’s reported date of expiration for this registration.TERMS OF USE: You are not authorized to access or query our Whois
database through the use of electronic processes that are high-volume and
automated except as reasonably necessary to register domain names or
modify existing registrations; the Data in VeriSign Global Registry
Services’ (“VeriSign”) Whois database is provided by VeriSign for
information purposes only, and to assist persons in obtaining information
about or related to a domain name registration record. VeriSign does not
guarantee its accuracy. By submitting a Whois query, you agree to abide
by the following terms of use: You agree that you may use this Data only
for lawful purposes and that under no circumstances will you use this Data
to: (1) allow, enable, or otherwise support the transmission of mass
unsolicited, commercial advertising or solicitations via e-mail, telephone,
or facsimile; or (2) enable high volume, automated, electronic processes
that apply to VeriSign (or its computer systems). The compilation,
repackaging, dissemination or other use of this Data is expressly
prohibited without the prior written consent of VeriSign. You agree not to
use electronic processes that are automated and high-volume to access or
query the Whois database except as reasonably necessary to register
domain names or modify existing registrations. VeriSign reserves the right
to restrict your access to the Whois database in its sole discretion to ensure
operational stability. VeriSign may restrict or terminate your access to the
Whois database for failure to abide by these terms of use. VeriSign
reserves the right to modify these terms at any time.The Registry database contains ONLY .COM, .NET, .EDU domains and
Registrars.
=-=-=-=Registration Service Provided By: Namecheap.com
Contact: support@namecheap.com
Visit: http://namecheap.comDomain name: factoryonlinegall.com
Registrant Contact:
WhoisGuard
WhoisGuard Protected ()Fax:
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
USAdministrative Contact:
WhoisGuard
WhoisGuard Protected (14172c57a5704e38b81372f4c155b466.protect@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
USTechnical Contact:
WhoisGuard
WhoisGuard Protected (14172c57a5704e38b81372f4c155b466.protect@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
USStatus: Locked
Name Servers:
ns1.2x4hosting.ru
ns2.2x4hosting.ruCreation date: 27 Dec 2012 01:19:00
Expiration date: 26 Dec 2013 17:19:00