
Backblaze is addressing the compatibility issue with newly released macOS Mojave.
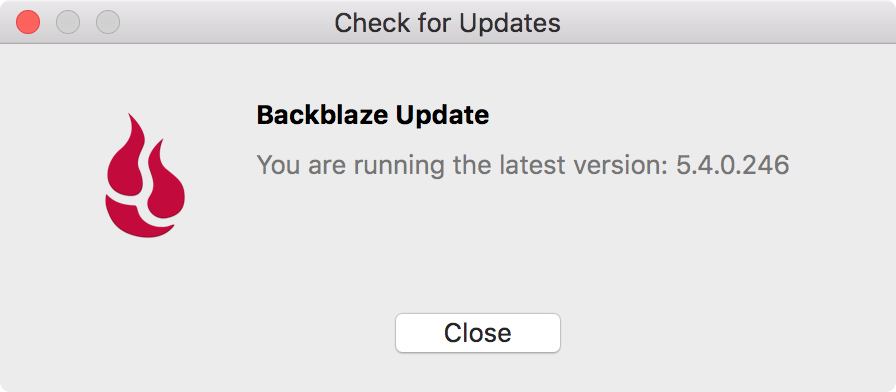
From Backblaze:


Celebrating 20 years of Nonsense, Powered by Natural Intelligence.
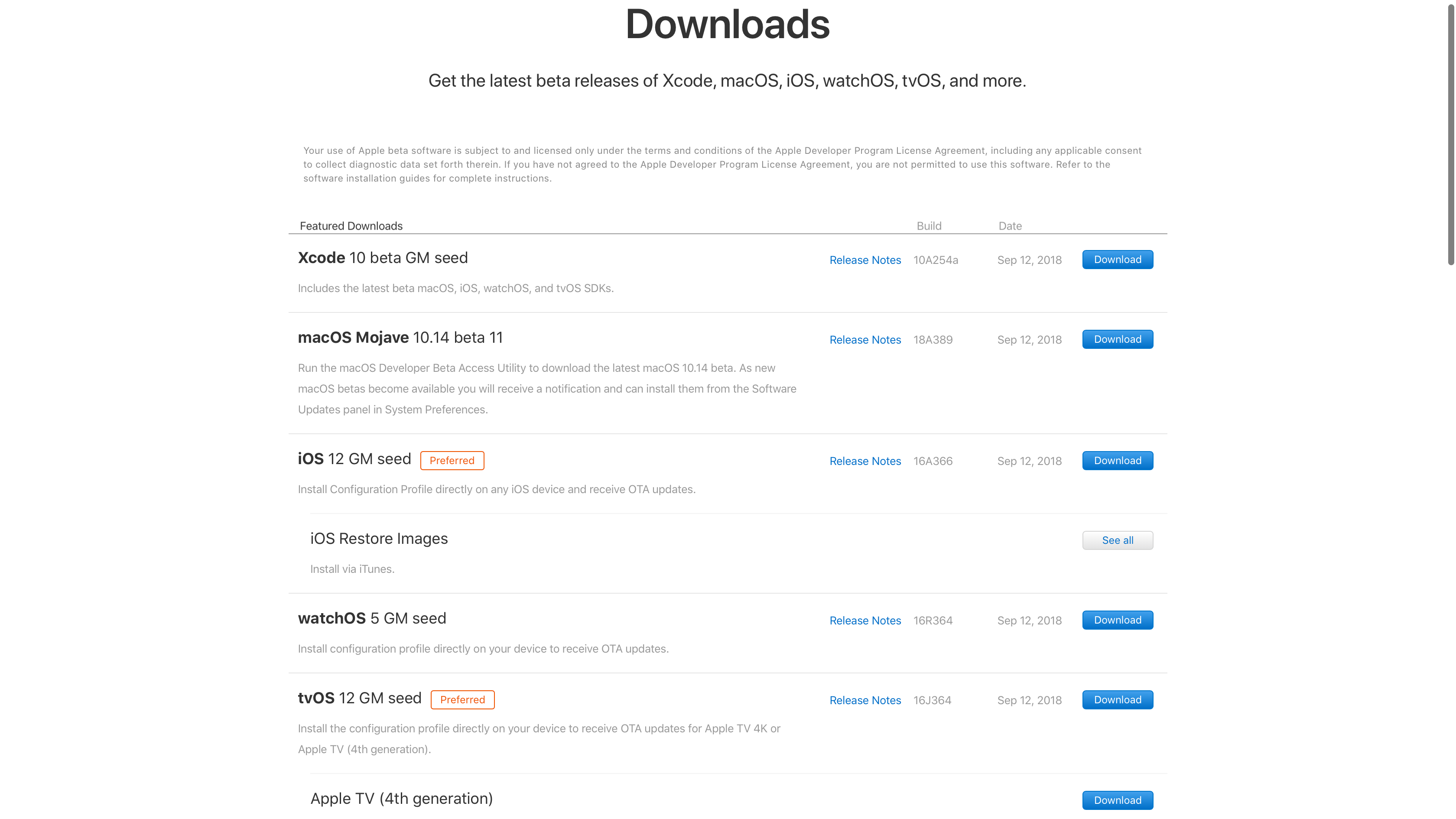
Following the conclusion of “Gather round” Special Event, Apple posts GM seeds of iOS 12, watchOS 5 and tvOS 12 along with macOS Mojave 11.4 beta 11.
One interesting note on macOS Mojave 11.4 beta 11 build 18A389, that it is believed to be the Release Candidate or even a GM seed.

Apple will be issuing Software Update to disable “root” user which is inadvertently enabled by default with blank password in macOS High Sierra.
To disable “root” user, follow the instruction from Apple or the instruction below:
Disable the root user
Choose Apple menu () > System Preferences, then click Users & Groups (or Accounts).Click the Lock, then enter an administrator name and password.
Click Login Options.
Click Join (or Edit).
Click Open Directory Utility.
Click the Lock in the Directory Utility window, then enter an administrator name and password.
From the menu bar in Directory Utility: Choose Edit > Disable Root
In previous incarnations of macOS/OS X/Mac OS X, “root” user is disabled by default.
Note:
Anyone with physical access to your Mac potentially can reset your password.

As reported by Juli Clover for MacRumors and numerous other sites:
The bug, discovered by developer Lemi Ergin, lets anyone log into an admin account using the username “root” with no password. This works when attempting to access an administrator’s account on an unlocked Mac, and it also provides access at the login screen of a locked Mac.
We verified that on macOS High Sierra 10.13.1, “root” user is enabled by default with blank password. For comparison, OS X El Capitan has “root” user disabled by default.
UPDATE:
We verified that previous versions of macOS/OS X/Mac OS X have “root” user disabled by default.
This is similar to the enabled-by-default-with-blank-password “administrator” accounts in Windows XP.
By having “root” user disabled by default, potentially a remote attacker can compromise Macs running macOS High Sierra.
Having said all that, anyone with physical access and the right knowledge can reset local user password.

A few days ahead the official iPhone X launch date, Apple releases iOS 11.1, watchOS 4.1, tvOS 11.1 and macOS High Sierra 10.13.1.
These updates includes fix for Key Reinstallation Attacks – KRACK vulnerability.
As we have reported on October 23, 2017 iOS 11.1 build 15B93 was indeed the Golden Master. In addition to that, iOS 11.1 for iPhone X carries a different build number.

Apple seeds macOS High Sierra Golden Master Candidate (build 15A372) on Thursday, September 14, 2017.
One of many known issues in macOS High Sierra is related to the new Apple File System (APFS):
- Some third-party applications may not correctly recognize volumes that are formatted using APFS.
We’re jumping in head-first, again, into the latest macOS High Sierra build. Let’s see waht else is still broken.
As usual, we always warn against installing major macOS (formerly Mac OS X and OS X) on essential productions computer. Yes, we’re talking about you, a recording studio that shall not be named here. ?

Apple is set to hold its first event at the Steve Jobs Theater at Apple Park today, September 12, 2017.
With the recent leaks, one can only wonder if Apple would have any surprises at all. According to an Apple employee who is definitely not Phil Schiller (@pschiller), *wink-wink*, there is one definite surprise for the event. There are some who call it a “preview”.
Apple will be streaming the event live at Apple.com and Apple TV.