UPDATE:
Apple updated the SSL Certificate for swscan.apple.com on early Sunday, May 25, 2014.
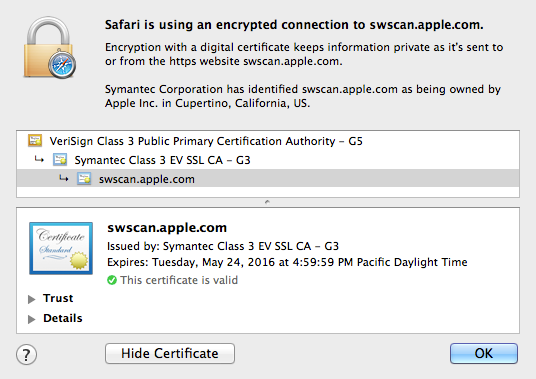
——-
Late Saturday afternoon, a colleague told me that he was having issues getting software updates through the Mac App Store.
An error has occurred
The certificate for this server is invalid. You might be connecting to a server that is pretending to be “swscan.apple.com” which could put your confidential information at risk.
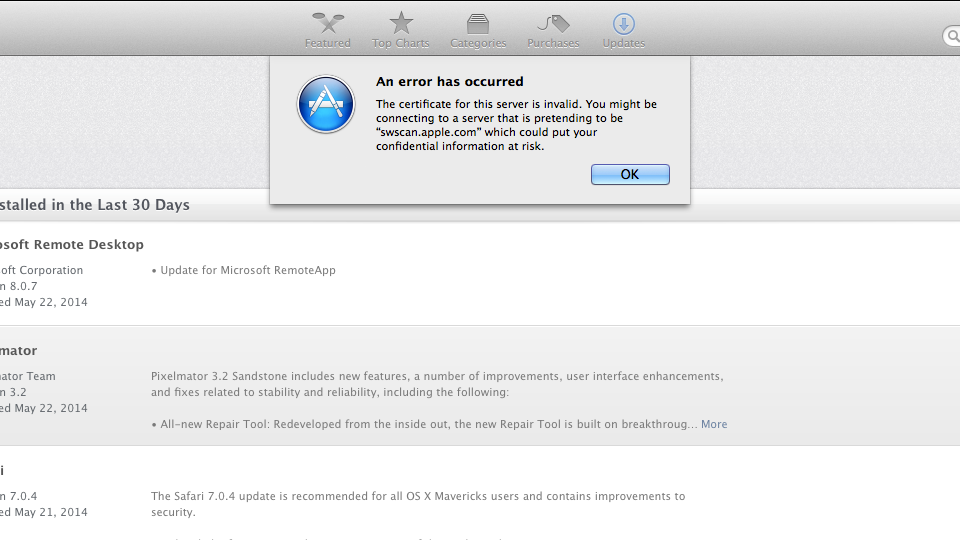
Upon further investigation, apparently someone at Apple forgot to install new SSL Certificate for swscan.apple.com.
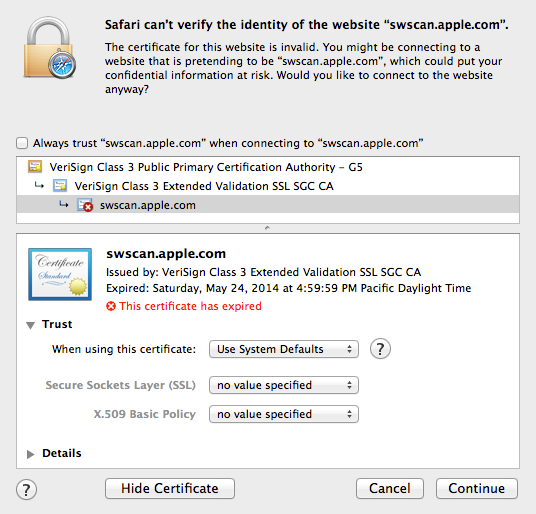
Is it possible that a small company like Apple could not afford at least one person to make sure all their security certificate up to date?
Mr Tim Cook, I am available to do the one job. How about $200,000 a year sound?