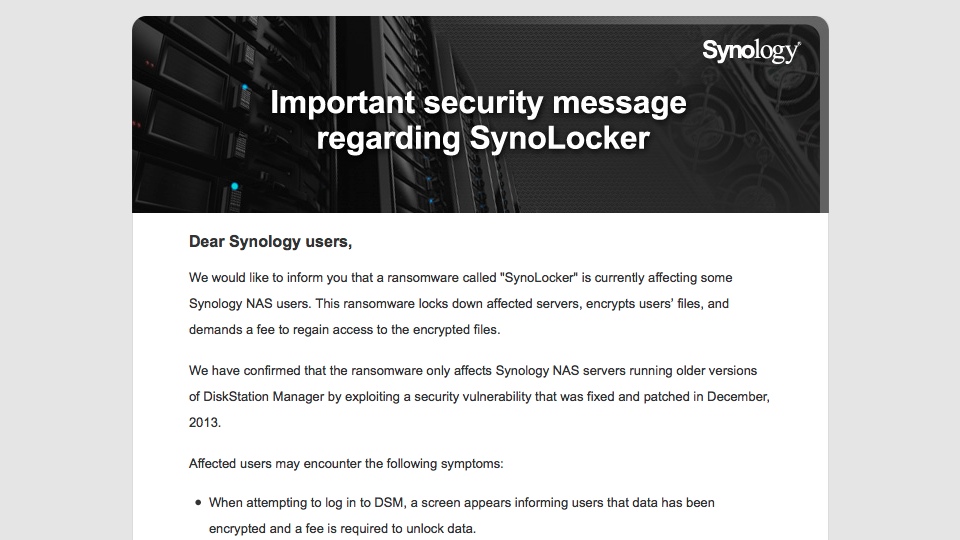
Synology has been sending users email regarding the SynoLocker ransomware, mirroring the statement posted at Synology website from August 5, 2014.
Dear Synology users,
We would like to inform you that a ransomware called “SynoLocker” is currently affecting some Synology NAS users. This ransomware locks down affected servers, encrypts users’ files, and demands a fee to regain access to the encrypted files.
We have confirmed that the ransomware only affects Synology NAS servers running older versions of DiskStation Manager by exploiting a security vulnerability that was fixed and patched in December, 2013.
Affected users may encounter the following symptoms:
- When attempting to log in to DSM, a screen appears informing users that data has been encrypted and a fee is required to unlock data.
- Abnormally high CPU usage or a running process called “synosync” (which can be checked at Main Menu > Resource Monitor).
- DSM 4.3-3810 or earlier; DSM 4.2-3236 or earlier; DSM 4.1-2851 or earlier; DSM 4.0-2257 or earlier is installed, but the system says no updates are available at Control Panel > DSM Update.
If you have encountered the above symptoms, please shutdown the system immediately and contact our technical support here: https://myds.synology.com/support/support_form.php
If you have not encountered the above symptoms, we strongly recommend downloading and installing DSM 5.0, or any version below:
- DSM 4.3-3827 or later
- DSM 4.2-3243 or later
- DSM 4.0-2259 or later
- DSM 3.x or earlier is not affected
You can manually download the latest version from our Download Center and install it at Control Panel > DSM Update > Manual DSM Update.
If you notice any strange behavior or suspect your Synology NAS server has been affected by the above issue, please contact us at security@synology.com.
We sincerely apologize for any problems or inconvenience this issue has caused our users. We’ll keep you updated with the latest information as we continue to address this issue.
Thank you for your continued patience and support.
Sincerely,
Synology Development Team
As a rule of thumb, Synology users should put their DiskStations behind firewalls and disable port forwarding for now. Make sure the DiskStations are running the latest version of DSM possible. More importantly, backup the content of the DiskStation.