New assignment arrived at the office earlier today. I am setting up Synology DS1621+ for the office to replace one of our old NAS. The package came with a few 16TB hard drives.

The DiskStation came with 4GB RAM, which I would add later.

Celebrating 20 years of Nonsense, Powered by Natural Intelligence.
New assignment arrived at the office earlier today. I am setting up Synology DS1621+ for the office to replace one of our old NAS. The package came with a few 16TB hard drives.

The DiskStation came with 4GB RAM, which I would add later.
Just a few weeks ago, I set up a Synology DS412+ Network Attached Storage with four Hitachi Deskstar NAS 4TB drives.


Using Synology Hybrid Raid, total storage available is about 11 Terabyte spanned across the four hard drives.
My colleague was having trouble with one of the two drives on his Synology DS710+ for quite some times. The troubled drive was finally replaced but not before we cleaned it off. To do that, I took the unit apart.

This unit actually has a VGA port, but we never plugged any monitor to it.
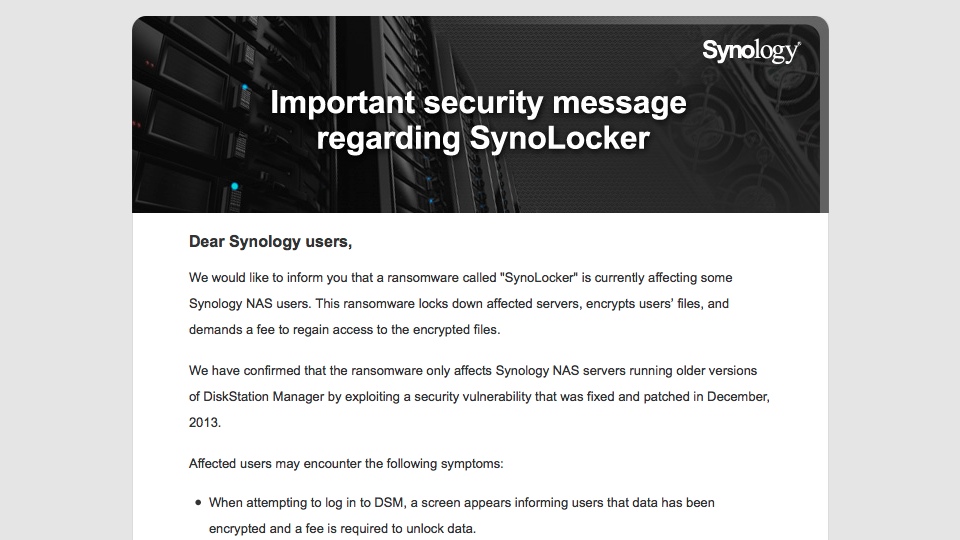
Synology has been sending users email regarding the SynoLocker ransomware, mirroring the statement posted at Synology website from August 5, 2014.
Dear Synology users,
We would like to inform you that a ransomware called “SynoLocker” is currently affecting some Synology NAS users. This ransomware locks down affected servers, encrypts users’ files, and demands a fee to regain access to the encrypted files.
We have confirmed that the ransomware only affects Synology NAS servers running older versions of DiskStation Manager by exploiting a security vulnerability that was fixed and patched in December, 2013.
Affected users may encounter the following symptoms:
- When attempting to log in to DSM, a screen appears informing users that data has been encrypted and a fee is required to unlock data.
- Abnormally high CPU usage or a running process called “synosync” (which can be checked at Main Menu > Resource Monitor).
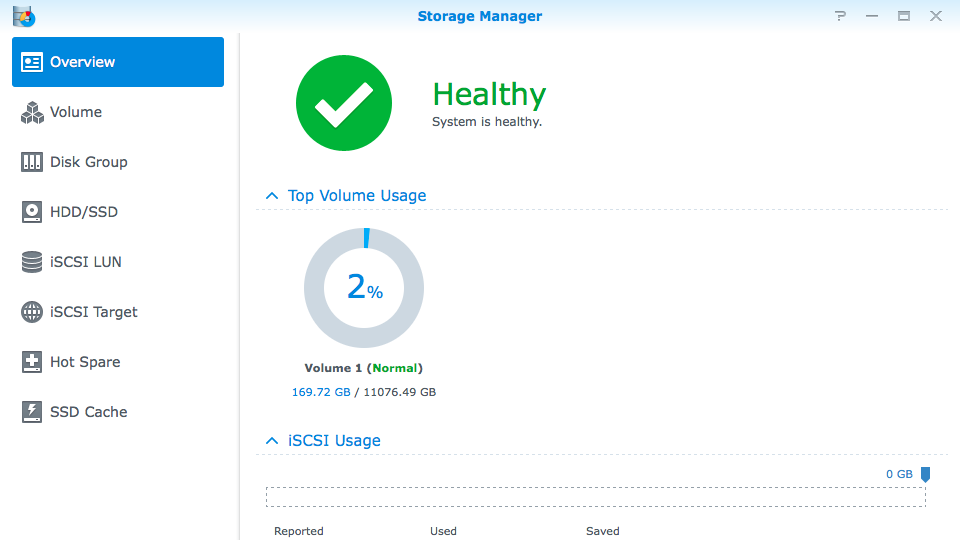
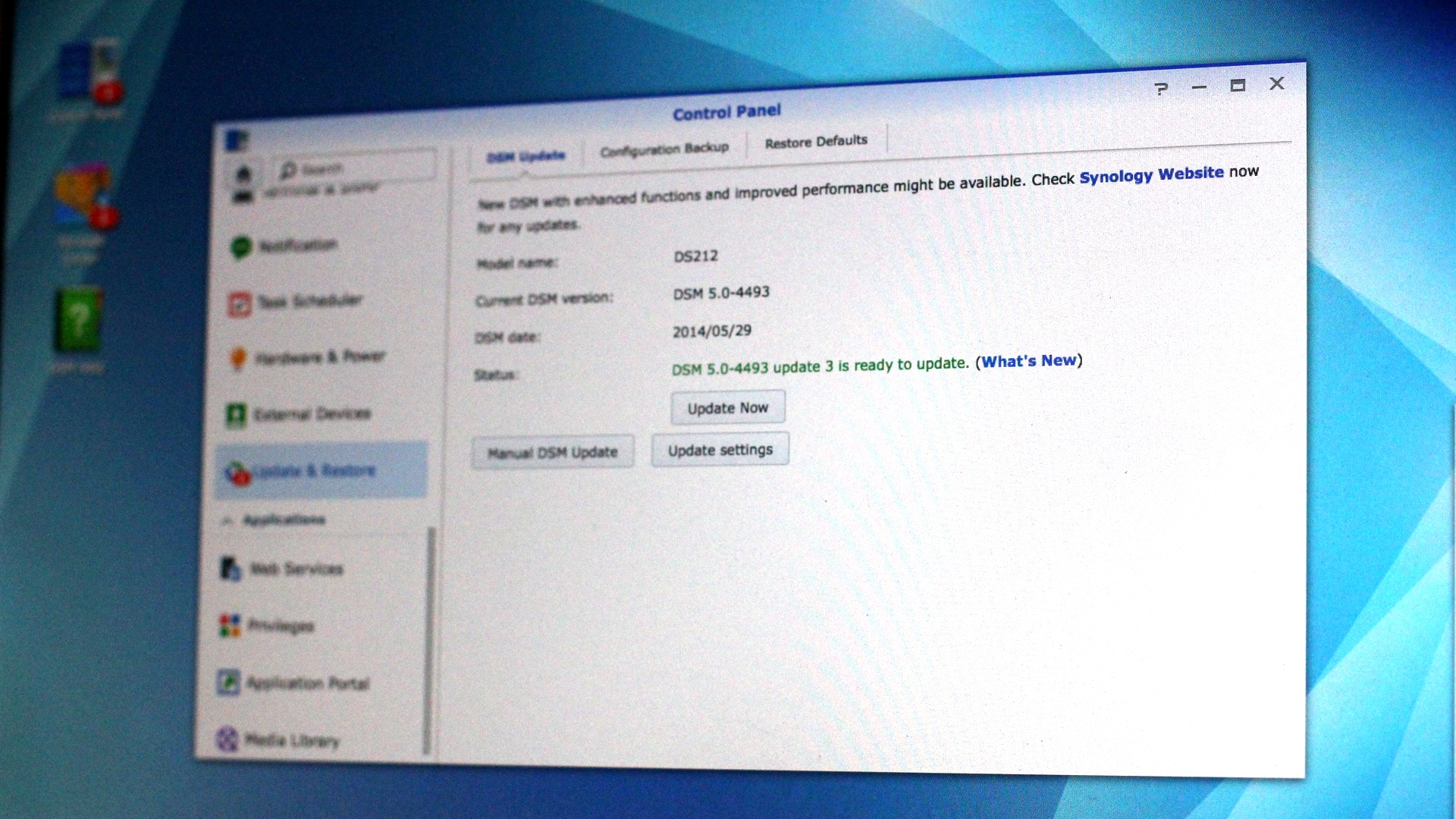
- DSM 4.3-3810 or earlier; DSM 4.2-3236 or earlier; DSM 4.1-2851 or earlier; DSM 4.0-2257 or earlier is installed, but the system says no updates are available at Control Panel > DSM Update.
If you have encountered the above symptoms, please shutdown the system immediately and contact our technical support here: https://myds.synology.com/support/support_form.php
If you have not encountered the above symptoms, we strongly recommend downloading and installing DSM 5.0, or any version below:
- DSM 4.3-3827 or later
- DSM 4.2-3243 or later
- DSM 4.0-2259 or later
- DSM 3.x or earlier is not affected
You can manually download the latest version from our Download Center and install it at Control Panel > DSM Update > Manual DSM Update.
If you notice any strange behavior or suspect your Synology NAS server has been affected by the above issue, please contact us at security@synology.com.
We sincerely apologize for any problems or inconvenience this issue has caused our users. We’ll keep you updated with the latest information as we continue to address this issue.
Thank you for your continued patience and support.
Sincerely,
Synology Development Team
As a rule of thumb, Synology users should put their DiskStations behind firewalls and disable port forwarding for now. Make sure the DiskStations are running the latest version of DSM possible. More importantly, backup the content of the DiskStation.
In the early Sunday morning of August 3, 2014, a tweet by Mike Evangelist was linked on Hacker News.
Lovely. My @Synology NAS has been hacked by ransomware calling itself Synolocker. Not what I wanted to do today. pic.twitter.com/YJ1VLeKqfY

I was somewhat scared by this news as some users at Synology forums reported that they were also victims of SynoLocker which is a CryptoLocker malware which specifically targets Synology NAS. I am managing numbers of Synology NAS for a few small offices and homes. Granted that none of them are directly connected to the Internet, but I have to make sure none of them would be hacked and crypto-locked.
Make sure your Synology NAS is running the latest DSM Operating System.
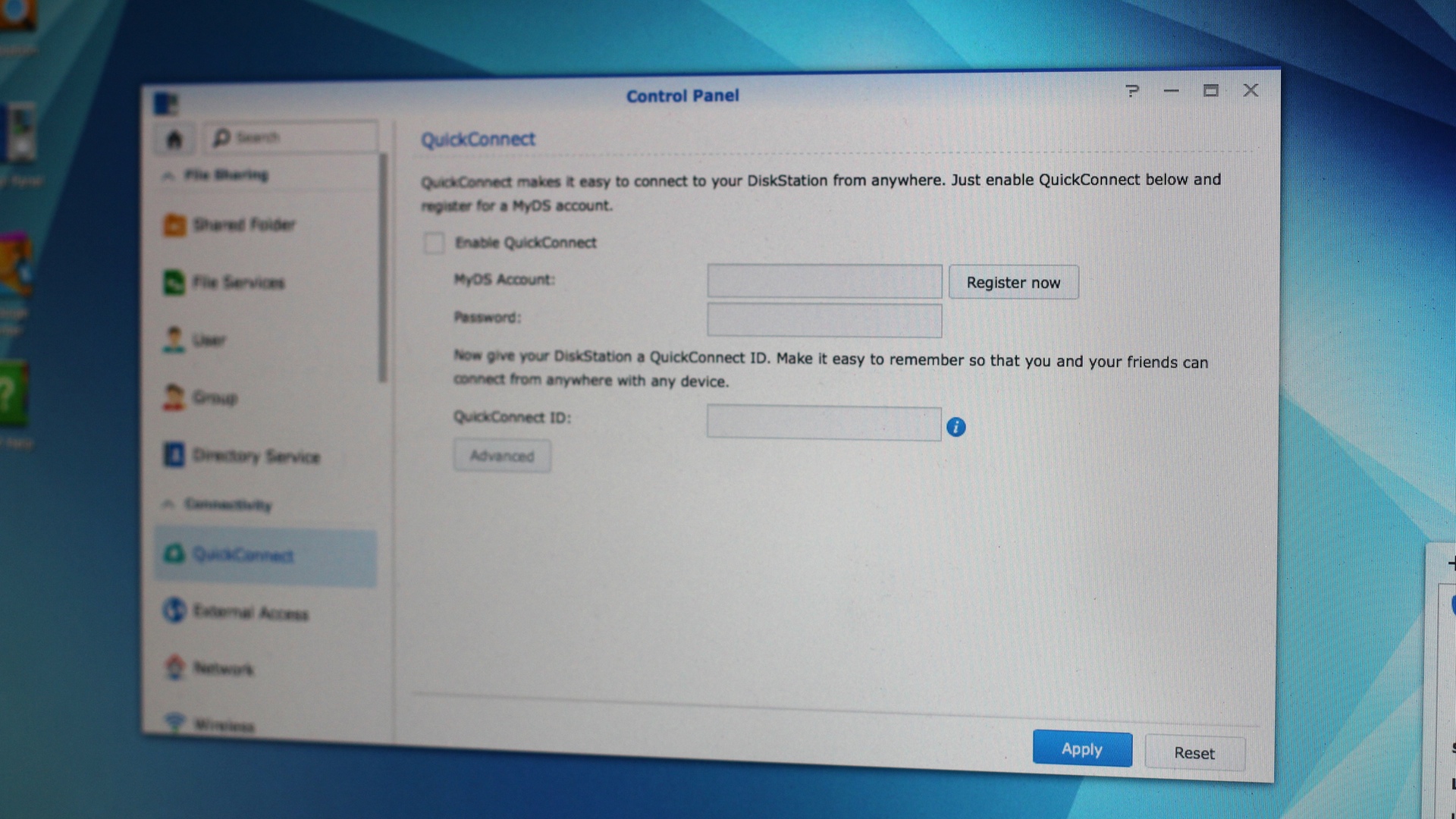
For now, disable the QuickConnect service.
Disable all port-forwarding if your Synology DiskStation is behind a NAT Firewall. This is a definite inconvenience; better to be safe than sorry.
More importantly, back-up the content of your Synology NAS. Should anything happen, you still have your data. My colleague has a great advice on backing up:
As always, if you have data on your Synology that you consider irreplaceable, make sure that you have it backed up to. I’d recommend using the built in Amazon S3 client. It’s cheap and fairly easy to set up, and should help you in case of a disaster.
I personally also run a backup to another hard drive locally for rapid recovery.