In the early Sunday morning of August 3, 2014, a tweet by Mike Evangelist was linked on Hacker News.
Lovely. My @Synology NAS has been hacked by ransomware calling itself Synolocker. Not what I wanted to do today. pic.twitter.com/YJ1VLeKqfY

I was somewhat scared by this news as some users at Synology forums reported that they were also victims of SynoLocker which is a CryptoLocker malware which specifically targets Synology NAS. I am managing numbers of Synology NAS for a few small offices and homes. Granted that none of them are directly connected to the Internet, but I have to make sure none of them would be hacked and crypto-locked.
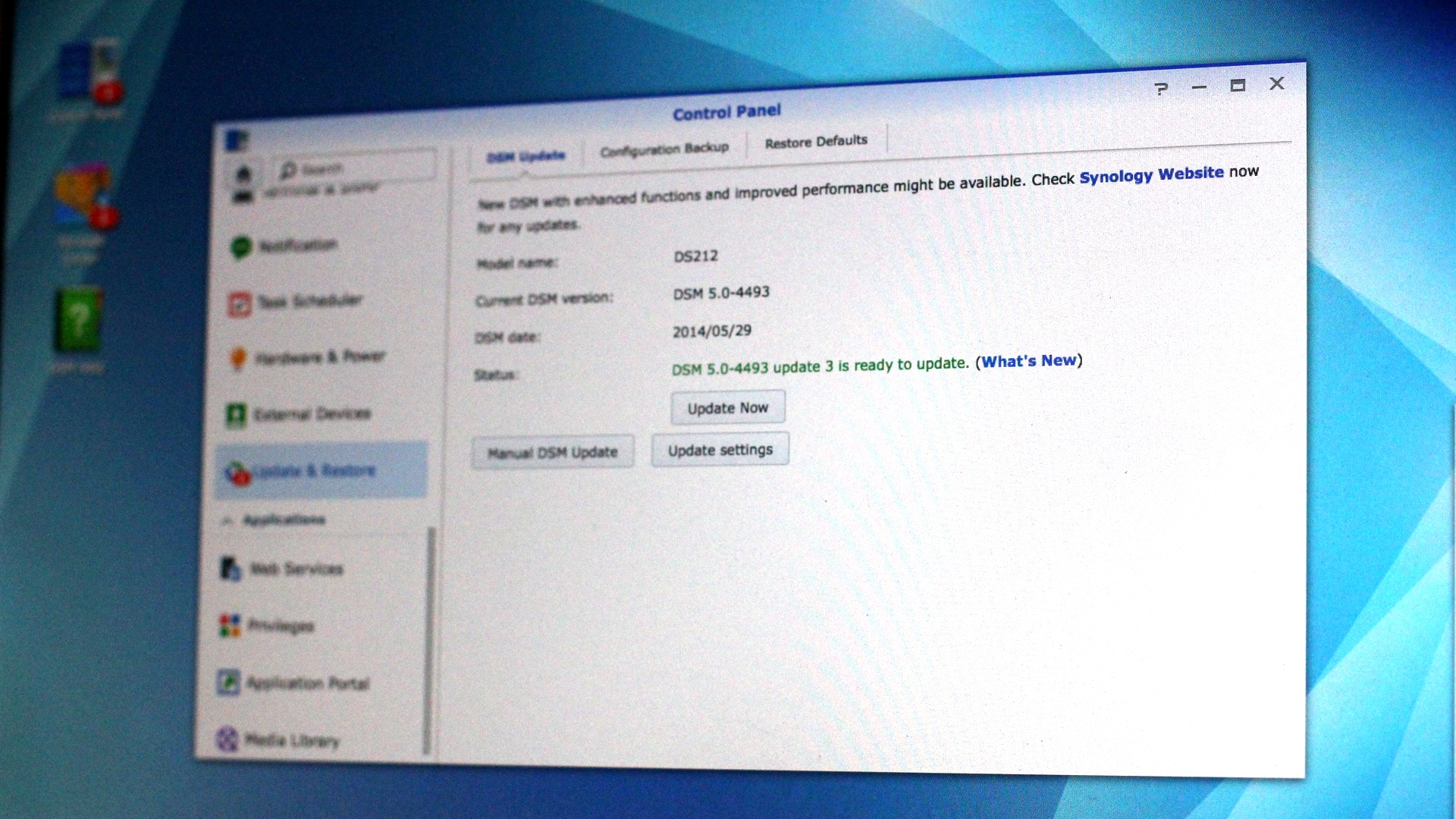
Make sure your Synology NAS is running the latest DSM Operating System.
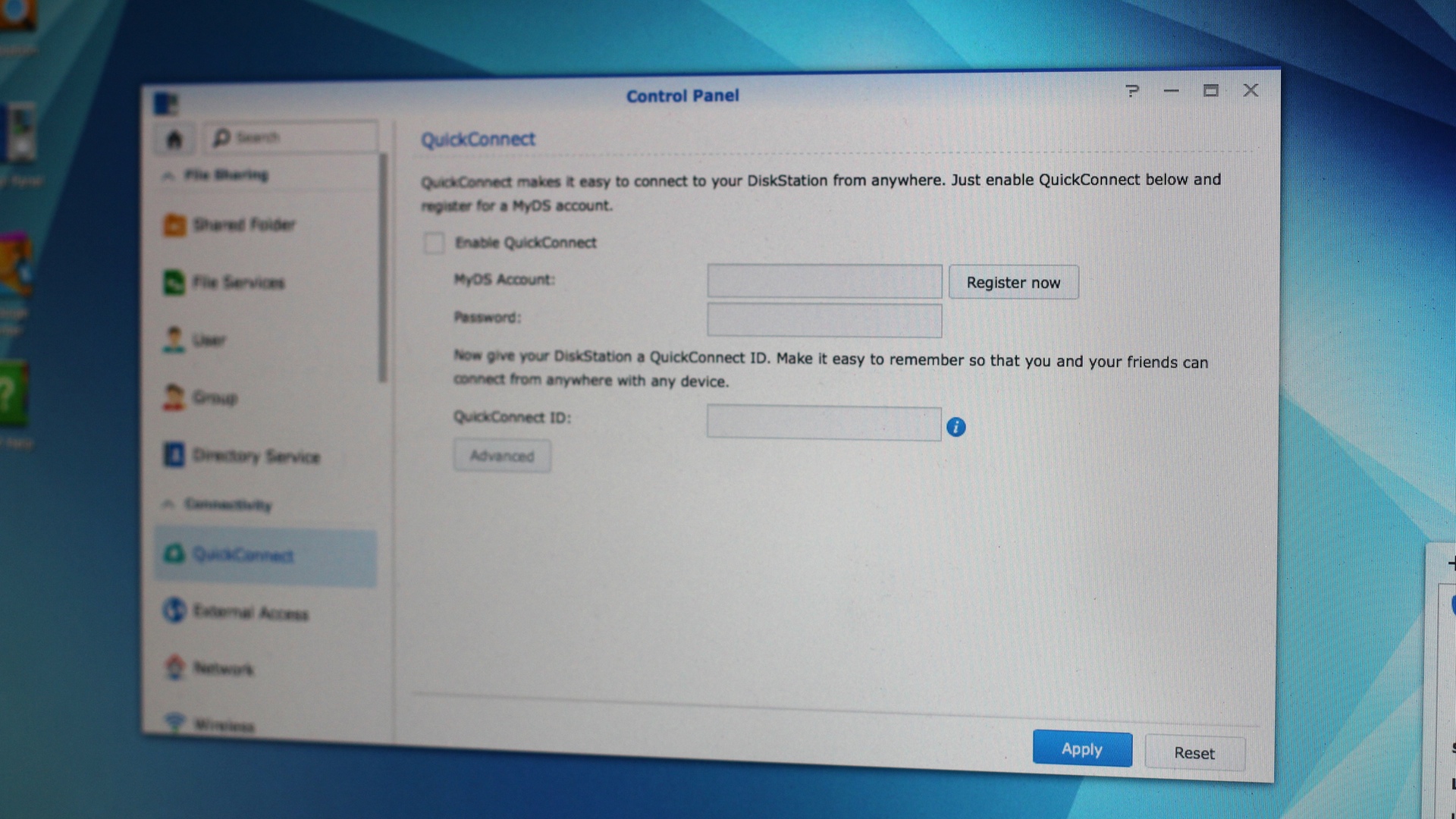
For now, disable the QuickConnect service.
Disable all port-forwarding if your Synology DiskStation is behind a NAT Firewall. This is a definite inconvenience; better to be safe than sorry.
More importantly, back-up the content of your Synology NAS. Should anything happen, you still have your data. My colleague has a great advice on backing up:
As always, if you have data on your Synology that you consider irreplaceable, make sure that you have it backed up to. I’d recommend using the built in Amazon S3 client. It’s cheap and fairly easy to set up, and should help you in case of a disaster.
I personally also run a backup to another hard drive locally for rapid recovery.
