Oracle releases Java 7 Update 11 to address vulnerability. If you do not need Java at all, it is advisable to uninstall it completely.
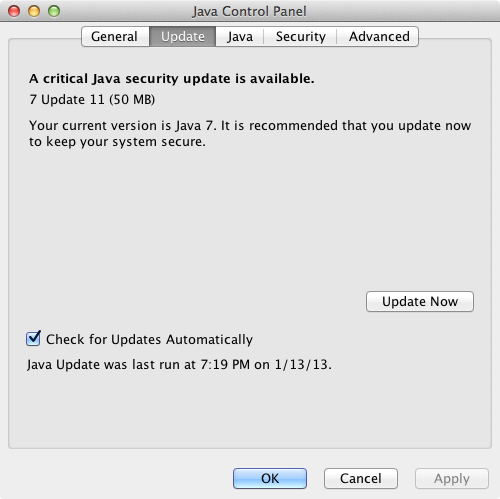
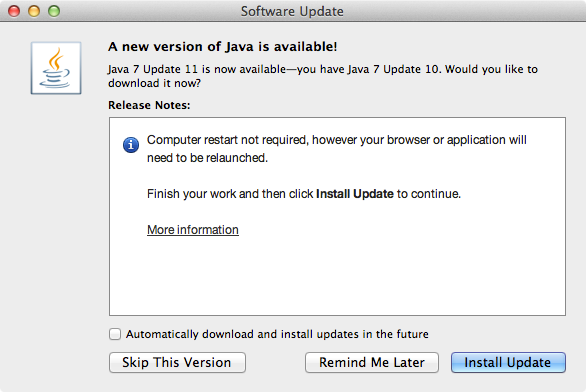
If the auto update failed, download Java 7 Update 11 manually.

Celebrating 20 years of Nonsense, Powered by Natural Intelligence.
Oracle releases Java 7 Update 11 to address vulnerability. If you do not need Java at all, it is advisable to uninstall it completely.


If the auto update failed, download Java 7 Update 11 manually.

Current news about Java vulnerabilities have been the talk of both tech and mainstream press. The U.S. Department of Homeland Security issued a warning of this vulnerability on Thursday January 10, 2013. On Friday January 11, 2013 we received numbers of called from users that their computers were infected by malware on that day. Security softwares such as Malwarebytes Anti-Malware and Microsoft Security Essentials detected the presence of malicious Java codes in the computers.
Companies like Apple and Mozilla Foundation have been pro-actively blocked Java on their platform.
This is certainly not the first time Java has been exploited to deliver malware. Back in August 2012 similar outbreak of malware used Java vulnerability as point of entry. Oracle says that they are preparing an update to Java to address the vulnerability.
So, I have successfully removed the ransomware/malware form the infected computer.
Booting the computer up to Safe Mode or Safe Mode with Networking would still activate the malware. That’s because it replaces the registry entry for Windows Shell from “Explorer.exe” to something else. So, boot the computer to “Safe Mode with Command Prompt” and type “regedit.exe” at the command prompt.
In registry editor, go to:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogon
In this particular case it was replaced with:
C:PROGRA~3dsgsdgdsgdsgw.bat
Delete the entry and replace it with:
Explorer.exe
Reboot the computer into “Safe Mode with Networking” and launch a web browser. Download, install and run the following programs if you haven’t already:
There are also other programs to scan and remove the malware.
Combofix detects that userinit.exe s also infected.
Microsoft Security Essentials also detected presence of Trojan:JS/Reveton.A, which was detected on January 11, 2013.
This computer was infected on Friday January 11, 2013, shortly after news about Java vulnerability was reported. After further investigations, I found that the infection happened through Java vulnerability. The infected computer had both Java 6 and 7 installed. Malwarebytes AntiMalware Free detected and removed the malicious Java module. Similar vulnerability was found back in August 2012.
Let’s take a look at the ransomware/malware.
It takes over Windows User Interface (UI) and replaces windows shell with the threatening message purporting from United States Department of Justice: “YOUR COMPUTER HAS BEEN LOCKED”
The message says that the computer has been locked for one or more violations:
They are pretty much the same language used in other ransomware/malware purporting from FBI, Police Cybercrime Investigation Department, etc. Some people might fall for this.
The malware also tries to activate the computer camera, for the purpose of scaring the user. Even though the infected computer doesn’t have any cameras installed, the malware pretends that it is recording video of the user.
The malware demands $300 to be paid in MoneyPak so users can unlock the computer.
So convenient that the malware tells you where to get this MoneyPak.
Anyway, you need to disable Java from your browsers.
If you’re using Mozilla Firefox, follow the instruction here: How to turn off Java applets
If you’re using Google Chrome, go to:
Settings > Privacy > Content Settings > Plug-ins > select “Click to play”
Also go to chrome://plugins/ to manually disable Java if necessary. (type in chrome://plugins/ in the address bar / omnibox)
If you are using Safari, go to:
Preferences > Security > uncheck “Enable Java”
If you are using Internet Explorer, follow the instruction from Sophos.

B.C. Rich presents Kerry King Cam playing War Ensemble
Aaron Swartz, 26, committed suicide on Friday January 11, 2013.
Swartz was known as one of co-founders of Reddit. In July 2011, Swartz was indicted by a federal grand jury for allegedly mass downloading documents from the JSTOR online journal archive with intent to distribute them.
It is a sad and confusing turn of event in the Tech community.
Commentaries:
I’ve gotten a call earlier today from a friend because his computer has been locked by “The United States Department of Justice”. In addition to that “The United States Department of Justice” demands computer owner to pay $300 to unlock the computer “avoid other legal consequences”.
First and foremost, The United States Department of Justice does not run such operation.
This is a ransomware. It replaces Windows 7 shell with its own executable file. Booting the computer to plain “Safe Mode” or” Safe Mode with Networking” will load the malicious executable. Instead, boot to “Safe Mode with Command Prompt” and manually remove the malicious software.
I’ll describe what I did in the next post.
Angry Birds Space gets an update on Thursday January 10th, 2013.
SPLASH! The Angry Birds have landed in the weirdest galaxy yet! All the planets are filled with water, strange aquatic life and worst of all — Bad Piggies in boats! Use the unique physics of these water planets to set up some fun trick shots! Also, check out the brand-new power-ups: Flock of Birds, Space Egg, and Pig Puffer! HINT: Make sure to check how Ice Bird and Pig Puffer react to water!
Make a splash in 30 NEW LEVELS!
Get ready for the ultimate underwater boss level!
Three-star levels for 3 new bonus levels!
Use Flock of Birds for a pack of destruction!
Create black holes with Space Egg!
Expand the pigs with Pig Puffer!
Check back daily for a free power-up!
Power-up specific leaderboards in addition to regular leaderboards!
iPhone / iPod touch | iPad | Android | Mac | Windows